Web Security Sales 101
How does this benefit our customers?
Akamai's Apps & API solution empowers customers to deliver fast, secure, and scalable digital experiences, ensuring optimal performance and protection for their applications and APIs
What Differentiation Do We Have?
Akamai's security platform delivers a comprehensive suite of capabilities in a single solution. It includes web application firewall (WAF), bot mitigation, API protection, and distributed denial-of-service (DDoS) defense.
Who Needs this Solution?
Organizations that develop and manage web applications and APIs, particularly in critical industries like finance, healthcare, and e-commerce, that rely heavily on APIs for seamless communication, data exchange, and core functionalities.
What is WAAP?
WAAP is an acronym for Web Application and API Protection – a security solution that protects against bad and undesirable traffic
App & API Protector Elevator Pitch
"AAP is the security solution that global brand’s trust to secure entire digital estates. Powered by the world’s largest global network, AAP simplifies the execution of comprehensive security providing Application and API Security, delivered with proactive automatic updates that self-tune for a hands-off experience. With industry-leading detections powered by our Adaptive Security Engine, AAP protects against bots, DDoS, zero-day threats, and more."
· Supporting Differentiators
o Many-in-One Solution
§ "Akamai’s AAP is a single solution with web application firewall, bot mitigation, API security, and DDoS protection as well as many customer-loved capabilities included such as Site Shield, mPulse Lite, EdgeWorkers, Image & Video Manager, API Acceleration, and more."
o Adaptive, Hands-Off Technology
§ "AAP’s comprehensive suite of security protections stay modern with proactive automatic updates and adaptive, self-tuning rules powered by machine-learning, hundreds of human threat experts, and the largest global network’s data. Integrate detection or vulnerability alerts into your DevOps workflows with Terraform or connect to SIEMs."
o The Power of ASE
§ "The Adaptive Security Engine, the technology at the core of App & API Protector, provides modern protection by combining machine learning, real-time security intelligence, advanced automation, and insights from over 400 threat researchers."
o API Security
§ "Secure beyond your applications with API Security protections against DDoS, malicious injection, credential abuse attacks, and API specification violations. The API Discovery capability alerts security teams to new, often unprotected, or modified APIs to keep your organization securely innovating."
o Industry-Leading Detections
§ "Detecting and mitigating attacks is the most important role of your organization's security solution. App & API Protector pioneers the market with analyst-recognized leading detections for DDoS, bot, malware, and more attack vectors."
How Web Application and API Protection works
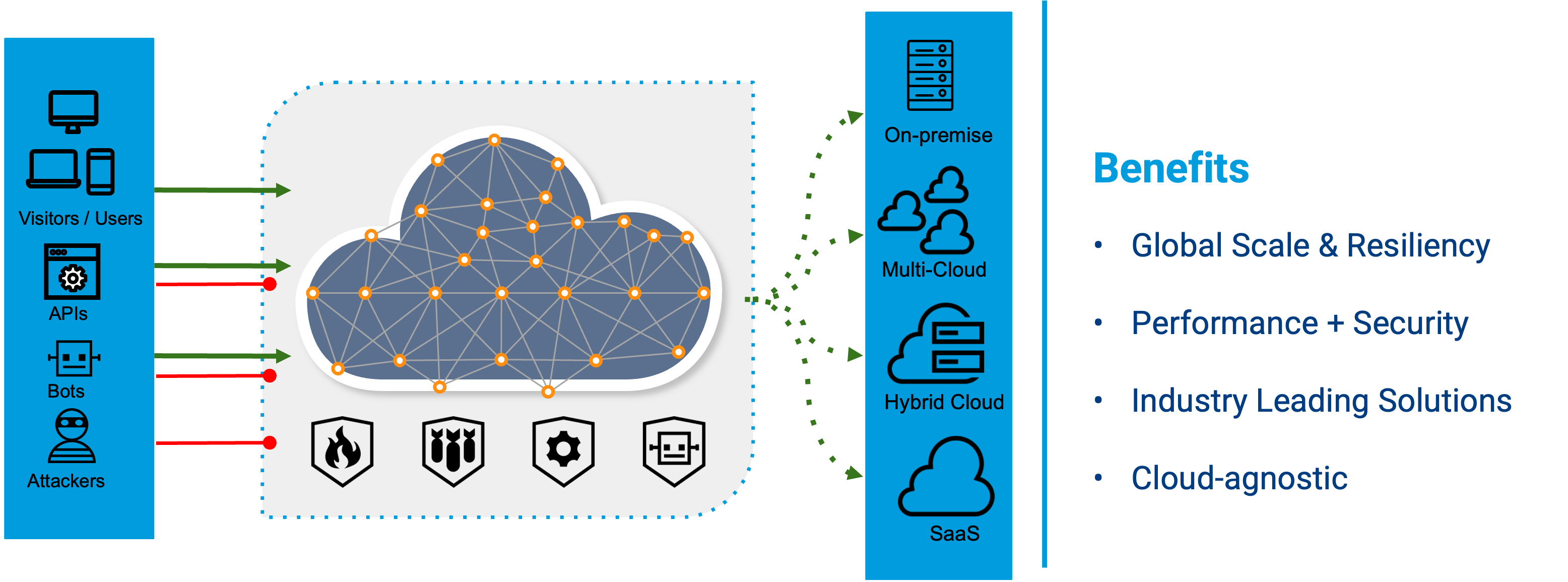
WAF then WAAP
· Evolved light years beyond the traditional WAF, Akamai’s WAAP, App & API Protector, delivers cutting edge solutions in:
o + DDoS Protection, Bot Visibility and Mitigation, Application Protections, API Protections
· Web Application Attacks
o App & API Protector protects against application abuse including SQL injection and XSS, as well as data exfiltration.
o Common Vulnerabilities and Exposures (CVE) Protection
§ Proactively shield your systems against known vulnerabilities, ensuring your web applications are secure.
o Rapid Zero Day Protection
§ Defend against emerging threats and vulnerabilities before they are widely known or patched.
o Personally Identifiable Information (PII) Data Protection
§ Safeguard from unauthorized access or exposure.
o Anomaly Detection
§ Detect and respond to abnormal activities or behaviors that may indicate a potential web attack.
o L3, L4, and L7 DDoS
§ Mitigate Distributed Denial of Service (DDoS) attacks targeting different layers of your networking systems.
o Advancing Vector Protection
§ Utilize advanced techniques to protect against evolving attack vectors and sophisticated threats.
· API Protection
o App & API Protector protects against malicious injection, credential abuse attacks, and API specification violations.
o API Discovery and Inventory
§ Maintain visibility and control over your APIs, ensuring only authorized access.
o PII Data Protection
§ Protect sensitive information exchanged through APIs from unauthorized access or misuse.
o Compliance Adherence
§ Help meet compliance regulations and standards governing API usage and data protection.
o API Abuse Protection
§ Block abusive patterns of API usage, preventing unauthorized access or exploitation.
o Rate Limiting on API Endpoints
§ Implement rate limiting controls to prevent abuse and ensure fair usage of your APIs.
o Anomaly Detection
§ Identify and respond to unusual or suspicious activities that may indicate API abuse or security threats.
· DoS/DDoS
o App & API Protector instantly drops network-layer DDoS attacks at the edge, protecting from both DDoS attacks and the traffic spikes of an attack.
o Application Layer (L7) and Network Layer (L3)
§ Volumetric attacks on these layers are automatically dropped at the Akamai Edge, preventing resource consumption as well as providing DDoS protection.
o Transport Layer (L4)
§ Mitigate transport-layer DDoS attacks, including UDP and TCP floods.
o Volumetric DDoS
§ Handle large-scale volumetric DDoS attacks by scaling resources and implementing traffic scrubbing.
o SlowPost Attacks
§ Detect and mitigate SlowPOST attacks, which aim to exhaust server resources by keeping connections open.
o Rate Limiting for App & API Traffic
§ Enforce rate limits to prevent abuse and ensure the availability of your applications and APIs.
· Bot Traffic
o Bot Visibility and Mitigation gives powerful detections to see good bots and let them through, while blocking bad bots.
o Bot Visibility
§ Enhance your understanding of bot presence of behavior with full traffic visibility and access to Akamai's expansive directory of more than 1,750 known bots.
o Good Bot Management
§ Ensure optimal performance for authorized bots.
o Mitigate Bots to Avoid Origin Overload
§ Safeguard your resources and implement cost savings by blocking unnecessary bots at the Edge.
o Lessen Skewed Visitor Analytics
§ Improve the accuracy of your visitor analytics and make better business decisions by filtering out unhelpful bot data.
· Has your business been subjected to a cyberattack or attacks? How concerned are you about the threat of cyberattacks?
· Has your business been impacted by the shortage of cybersecurity professionals?
· How much time or effort is required to maintain your security solution?
· Are you concerned that your firewalls are inadvertently blocking legitimate customers or end users from using your applications?
· What are your compliance requirements?
· Does your WAF have API Protections?
· Are you able to see bot traffic and block unwanted automated traffic to realize resource savings today?
Customer Challenges
· Common and Zero-Day Application Vulnerabilities
o Challenge: Applications are often vulnerable to common threats and zero-day exploits which can be difficult to detect and mitigate.
o Solution: The Adaptive Security Engine provides automatic, adaptive and effective security leveraging the threat intelligence of the Akamai Connected Cloud Platform and hundreds of threat experts.
· API Discovery and Protection
o Challenge: APIs are increasingly becoming targets for attacks, and there’s a need to discover, validate, and protect these APIs to prevent data breaches and misuse.
o Solution: Akamai’s API Protections automatically discover APIs, validate API traffic, and report on Personally Identifiable Information (PII), thereby providing comprehensive API security
· Bot Attacks and Resource Drain
o Challenge: Automated threats and malicious bots can lead to service abuse, automated attacks, and resource drain.\
o Solution: Akamai’s Bot Protections in BVM (Bot Visibility & Mitigation) offer visibility into bot traffic and mitigate automated threats, improving the security and performance of web properties.
· Malware and Data Leaks
o Challenge: Malware-infected files and data leaks, particularly involving PII, can compromise the security of applications and user data.
o Solution: Malware Protection and PII Handling Alerts automatically scan file uploads at the edge for malware and enforce constraints on PII to prevent data leaks and ensure compliance.
· Operational Burden and Manual Tuning
o Challenge: Constantly updating and tuning security policies manually is time-consuming and resource-intensive.
o Solution: Akamai’s Adaptive Security Engine (ASE) automates these processes with self-tuning capabilities, reducing manual effort and ensuring that security policies are always up-to-date.
· Real-time Threat Intelligence and Visibility
o Challenge: Keeping up with emerging threats requires extensive threat intelligence and visibility into traffic patterns.
o Solution: Akamai’s extensive network provides real-time visibility and threat intelligence, leveraging a vast database and the expertise of human threat hunters to stay ahead of new threats.
Objection Handling
· The customer points out that a solution from a competitor is more inexpensive.
o You can reply that the competitor may be cheaper at the expense of capability/controls. Use this as an opportunity to dig deeper into security. Use this objection as an opportunity to explain the value of investing in a solution with Akamai.
· The customer says that they do not need to pay integration fees with anyone else. Why pay with Akamai?
o Explain integration options to the customer. The reason for fees is to integrate AAP quickly, giving the customer a higher ROI.? Use this objection as an opportunity to showcase Akamai's ability to do fast integration.
· A customer knows they are paying well above market rate for AAP.
o Address the issue before renewal. Perhaps include a new product to level out the reduction. Use this objection as an opportunity to build trust and show empathy via proactivity.
· Global Scale and Intelligence - Akamai has unparalleled insight due to the visibility provided by the Akamai Edge. This is becoming especially important as we move into an AI-driven world. Akamai's unparalleled proprietary data drives threat intelligence.
· Adaptive Security Engine - Less hands-on management of security policies with automated protections that are tailored for each customer's threat landscape (resulting in fewer false positives) and self-tuning capabilities. Adaptive Security Engine provides great value over WAFs run by rule sets, which can require manual tuning, have issues scaling, and can be slow to protect.
Comparative Differentiators
· Access to more data enables higher accuracy from WAAP rules, ML algorithms, and other detections.
· Global scale and distribution improves network reliability and availability of application performance even during attacks. This is important for customers who have very low risk tolerance.
· Higher detection accuracy with an adaptive security engine and risk-scoring model that goes beyond static rulesets like OWASP ModSecurity Core Rule Set.
· Customers seek to improve their API protections with defined API specifications (positive API security model). This capability is not widely available among WAF/WAAP competitors.
Holistic Differentiators
· Very low vendor risk. Akamai is unlikely to go out of business/exit the product space/have a corporate disruption that suddenly leaves the customer with no product or no support.
· Value from Akamai products continues over the entire lifecycle as products are constantly updated and innovations incorporated; no worry of having products unable to keep up with changing needs.
· Greater network effect as customers benefit from detections and mitigations learned from stopping the most sophisticated attacks on the world’s largest companies. Customers can manage all their Akamai entitlements from a single UI.
· Akamai's industry-recognized Threat Research team often identifies new and evolving threats before competitors.
· Provides customer confidence with Akamai's long-standing security experience.
· capable Akamai experts are accessible from basic technical support to fully managed security operations, providing greater peace-of-mind and customer support.
|
App & API Protector (AAP) |
AAP - Included Delivery |
AAP - Included Advanced Delivery |
AAP w/ ASM - Included Delivery |
AAP w/ ASM - Included Advanced Delivery |
||||||
|
SIEM Integration |
Included |
Included |
Included |
Included |
||||||
|
Security Configuration (SC) |
1 |
1 |
10 |
10 |
||||||
|
Security Policy per SC |
10 |
10 |
20 |
20 |
||||||
|
Rate Policies |
15 |
15 |
15 |
15 |
||||||
|
Custom rules |
100 |
100 |
Unlimited |
Unlimited |
||||||
|
Adaptive Security Engine |
Auto, self-tuning |
Auto, self-tuning |
Auto, Manual, self-tuning |
Auto, Manual, self-tuning |
||||||
|
API Security |
Auto inspection + Positive |
Auto inspection + Positive |
Auto inspection + Positive |
Auto inspection + Positive |
||||||
|
Bot visibility & Mitigation |
Yes |
|||||||||
|
Site Shield |
Yes |
|||||||||
|
API Discovery |
Yes |
|||||||||
|
Client Reputation |
N/A |
N/A |
Yes |
Yes |
||||||
|
Delivery module |
DSA |
ION |
DSA |
ION |
||||||
|
mPulse lite |
1 million beacon |
|||||||||
|
Include Entitlements |
''3 Million Hits''
Image and Video Manager - Image Optimization, ''10,000 Million Hits'' API Acceleration |
|||||||||
|
Cost |
$ |
$$ |
$$$ |
$$$$ |
||||||
AAP
Pricing Example
|
Item |
Example |
Unit of Price |
|
Product |
AAP Included Delivery |
|
|
Included |
1 domain, 15 RP, 1SC, 1 SS Map, DV SAN
SNI(Cert), mPulse lite |
|
|
Traffic |
10TB (Traffic Tier(TB):1,2,5,10
~ Unlimited) |
Million Hits Plus GB, GB, or Mbps |
|
Add-on |
Malware Protection |
N/A |
|
SSL Cert |
DV-SNI(1k), DV-SAN-SNI(100),
EV-SAN SNI(25), OV-SAN-SNI(25), OV-Wildcard-SNI(25),
OPV-Wildcard-SAN-SNI(N/A), Third-party-SNI(25) |
$0 + Custom |
|
Digital Price |
https://products.akamai.com |
|
